
最近拿到网络配置实训的题目,其主要包含设备配置部分和服务器配置部分,都拿来认真的做了一下,准备做一次完整的记录(保不定以后就摸不到交换机路由器了)。
此篇主要讲述的是设备的配置与规划,服务器的配置部分其实比较简单,且大互联网都能找到。文档比较长主要需求点如下:
该项目中分别由总公司网络和分公司网络两部分组成;总公司有人事部、财务部、销售部和技术部四个部门,杭州分公司设有销售二部。
总公司的网络采用双核心架构,以实现网络的高可用性和高可靠性,并采用双出口的网络接入模式,都使用路由器接入城域网和互联网。允许 SOHO 办公和出差的员工能够方便、快捷、安全的访问总公司内网服务器群。
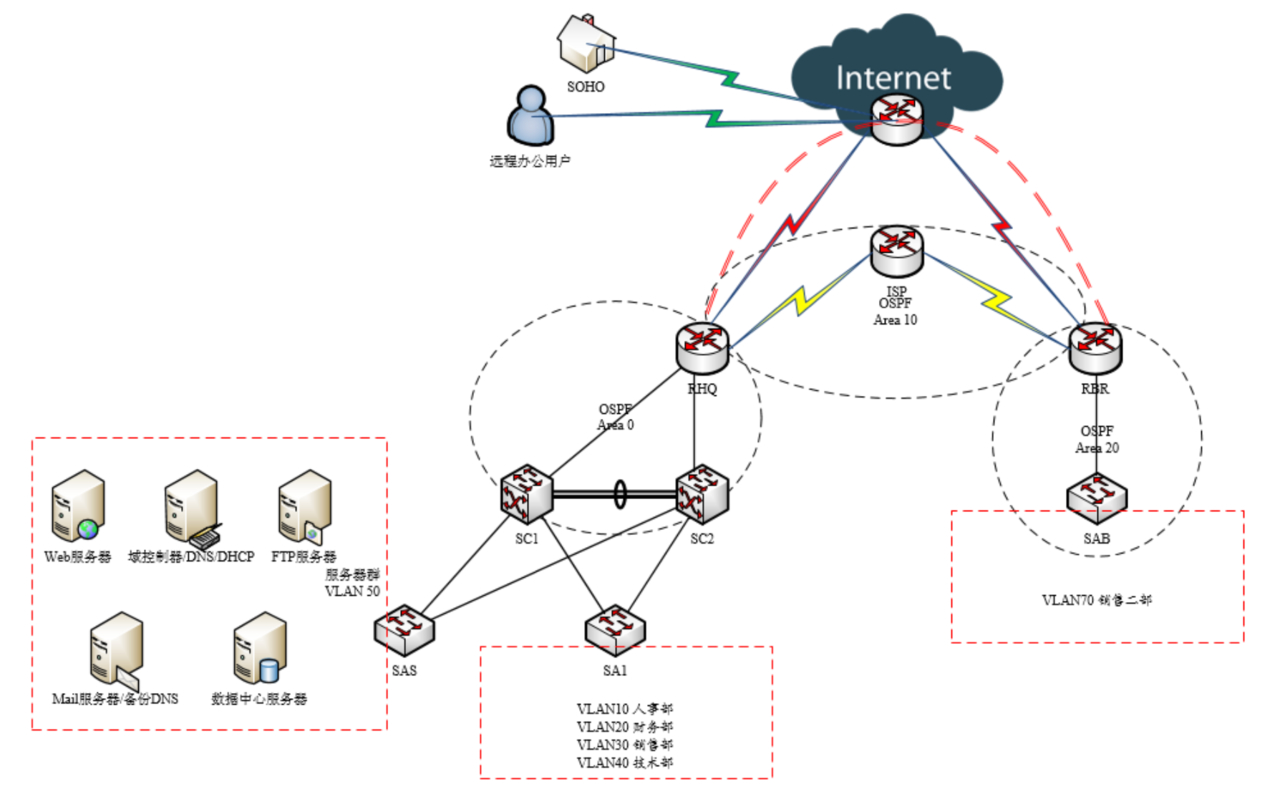
根据上门的拓扑图在 GNS 中进行规划连线转化为下面的有详细说明的拓扑结构,包括接口地址,VLAN 地址、OSPF 区域都有详细的标注,这是在配置之前比较关键的一步。
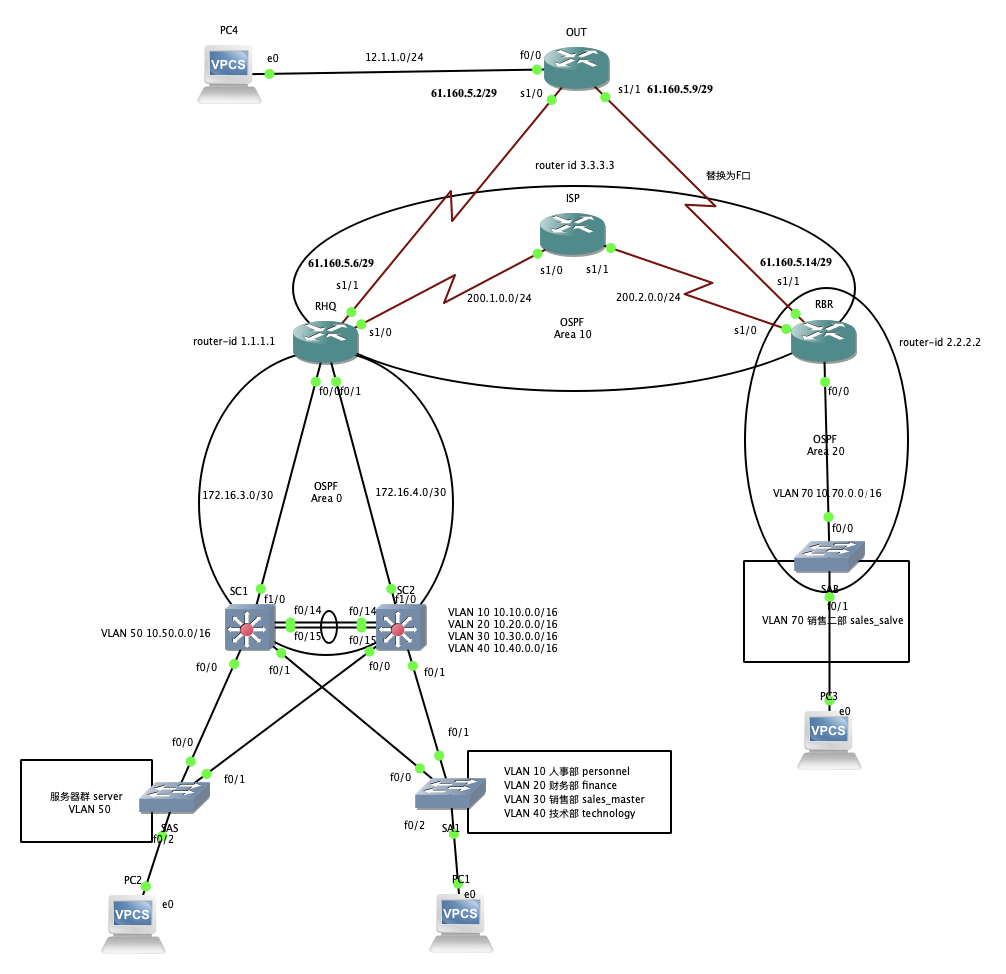
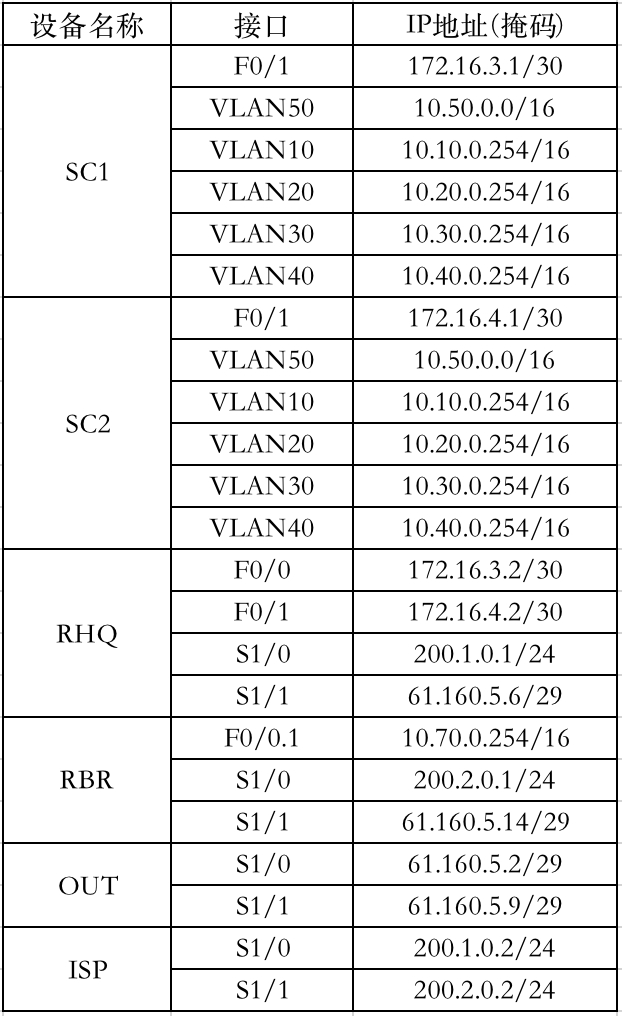
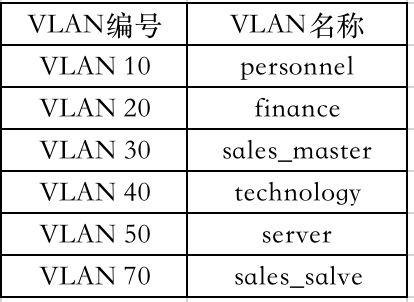
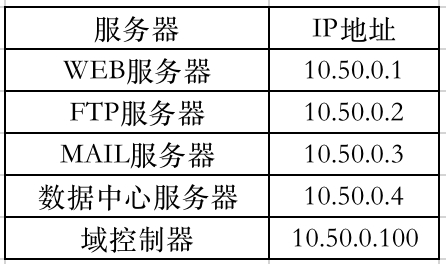
最后通过上图整理一份详细的接口地址表、VLAN 名称表和服务器地址表
做好这些拓扑规划之后,还必须适配真实实验室的环境。这个时候问题就出现了。
第一个问题,拓扑中一共需要三台交换机设备,而实验室机柜缺一台,此时考虑将分公司的交换机去掉改成直连路由器。
第二个问题,实验室设备的中路由器一共四台,且串口线已经两两相连,无法改动,此时只能按照实验室设备的摆放规划哪台路由器需要做什么。
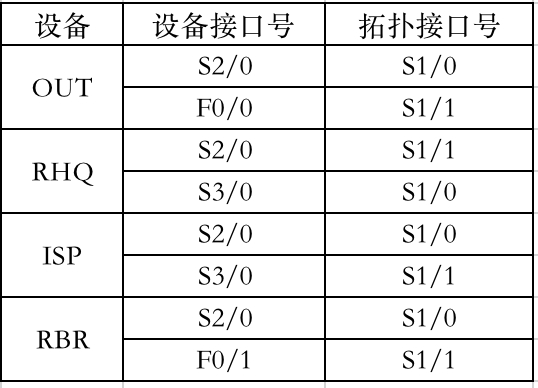
第三个问题是有两台路由器只有一个 S 口,此时需要考虑用 F 口替代,下表即指定了哪些接口替代哪些接口的具体方案。
问题还是挺多的,整理完这些问题之后就可以上手配置了。
此时需要一条 Console 线,Windows 系统可以考虑用 SCRT 或者 PUTTY 连接,而 Mac 系统的话只需要下面这条命令连接设备。
screen /dev/cu.usbserial-AH06DB0K 9600
该命令其实也意为指定 Console 口和波特率。
基础配置即一些接口地址的配置,有了前面地址表的完整规划之后,配置也就非常的方便了。
interface Serial 2/0
ip address 61.160.5.2 255.255.255.248
clock rate 64000
!
interface FastEthernet 0/0
ip address 61.160.5.9 255.255.255.248
!
interface FastEthernet 0/1
ip address 12.1.1.254 255.255.255.0
!
interface Serial 2/0
ip address 200.1.0.2 255.255.255.0
!
interface Serial 3/0
ip address 200.2.0.2 255.255.255.0
clock rate 64000
!
interface Serial 2/0
ip address 61.160.5.6 255.255.255.248
!
interface Serial 3/0
ip address 200.1.0.1 255.255.255.0
clock rate 64000
!
interface FastEthernet 0/0
ip address 172.16.3.2 255.255.255.252
!
interface FastEthernet 0/1
ip address 172.16.4.2 255.255.255.252
!
interface Serial 2/0
ip address 200.2.0.1 255.255.255.0
!
interface FastEthernet 0/0
ip address 10.70.0.254 255.255.0.0
!
interface FastEthernet 0/1
ip address 61.160.5.14 255.255.255.248
!
interface Loopback 0
ip address 2.2.2.2 255.255.255.255
!
配置完路由器接口,接着配置一下交换机的 VLAN,和三层交换机 VLAN 的接口,此时的 VLAN 的名称和地址需要根据接口地址表和 VLAN 名称表配置,也相对简单。
vlan 10
name personnel
!
vlan 20
name finance
!
vlan 30
name sales_master
!
vlan 40
name technology
!
vlan 50
name server
!
interface FastEthernet 0/2
switchport access vlan 50
!
interface FastEthernet 0/3
switchport access vlan 50
!
interface FastEthernet 0/10
switchport mode trunk
!
vlan 10
name personnel
!
vlan 20
name finance
!
vlan 30
name sales_master
!
vlan 40
name technology
!
vlan 50
name server
!
interface FastEthernet 0/1
switchport mode trunk
!
interface FastEthernet 0/2
switchport access vlan 10
!
interface FastEthernet 0/3
switchport access vlan 20
!
interface FastEthernet 0/4
switchport access vlan 30
!
interface FastEthernet 0/5
switchport access vlan 40
!
interface FastEthernet 0/10
switchport mode trunk
!
vlan 10
name personnel
!
vlan 20
name finance
!
vlan 30
name sales_master
!
vlan 40
name technology
!
vlan 50
name server
!
interface FastEthernet 0/1
switchport mode trunk
!
interface FastEthernet 0/10
switchport mode trunk
!
VRRP 只需要在每个 VLAN 接口下配置虚拟 IP 和优先级即可,SC1 VLAN50 的优先级为 120,其余为默认的 100,而 SC2 正好与 SC1 相反配置。
interface VLAN 10
ip address 10.10.0.253 255.255.0.0
vrrp 1 ip 10.10.0.252
!
interface VLAN 20
ip address 10.20.0.253 255.255.0.0
vrrp 2 ip 10.20.0.252
!
interface VLAN 30
ip address 10.30.0.253 255.255.0.0
vrrp 3 ip 10.30.0.252
!
interface VLAN 40
ip address 10.40.0.253 255.255.0.0
vrrp 4 ip 10.40.0.252
!
interface VLAN 50
vrrp 5 priority 120
vrrp 5 ip 10.50.0.252
!
interface VLAN 10
ip address 10.10.0.254 255.255.0.0
vrrp 1 priority 120
vrrp 1 ip 10.10.0.252
!
interface VLAN 20
ip address 10.20.0.254 255.255.0.0
vrrp 2 priority 120
vrrp 2 ip 10.20.0.252
!
interface VLAN 30
ip address 10.30.0.254 255.255.0.0
vrrp 3 priority 120
vrrp 3 ip 10.30.0.252
!
interface VLAN 40
ip address 10.40.0.254 255.255.0.0
vrrp 4 priority 120
vrrp 4 ip 10.40.0.252
!
interface VLAN 50
ip address 10.50.0.254 255.255.0.0
vrrp 5 ip 10.50.0.252
!
MSTP 需要在四个交换机上都配置一下,并且在三层交换机声明一下主备。
spanning-tree
spanning-tree mst configuration
revision 1
name MSTP
instance 0 vlan 1-9, 11-19, 21-29, 31-39, 41-49, 51-4094
instance 10 vlan 10, 20
instance 20 vlan 30, 40
instance 30 vlan 50
!
spanning-tree
spanning-tree mst configuration
revision 1
name MSTP
instance 0 vlan 1-9, 11-19, 21-29, 31-39, 41-49, 51-4094
instance 10 vlan 10, 20
instance 20 vlan 30, 40
instance 30 vlan 50
spanning-tree mst 10 priority 4096
spanning-tree mst 20 priority 4096
spanning-tree mst 30 priority 0
!
SC2
spanning-tree
spanning-tree mst configuration
revision 1
name MSTP
instance 0 vlan 1-9, 11-19, 21-29, 31-39, 41-49, 51-4094
instance 10 vlan 10, 20
instance 20 vlan 30, 40
instance 30 vlan 50
spanning-tree mst 10 priority 0
spanning-tree mst 20 priority 0
spanning-tree mst 30 priority 4096
!
OSPF 配置需要注意的是 router-id 的配置,OSPF 虚链路的配置,以及虚链路的 MD5 加密。
router ospf 10
router-id 3.3.3.3
network 200.1.0.0 0.0.0.255 area 10
network 200.2.0.0 0.0.0.255 area 10
!
router ospf 10
router-id 1.1.1.1
network 10.99.0.0 0.0.255.255 area 0
network 172.16.3.0 0.0.0.3 area 0
network 172.16.4.0 0.0.0.3 area 0
network 200.1.0.0 0.0.0.255 area 10
area 10 virtual-link 2.2.2.2 authentication message-digest
area 10 virtual-link 2.2.2.2 message-digest-key 1 md5 cisco123
default-information originate always metric 150
!
ip route 0.0.0.0 0.0.0.0 Serial 2/0
!
router ospf 10
router-id 2.2.2.2
network 10.70.0.0 0.0.255.255 area 20
network 200.2.0.0 0.0.0.255 area 10
area 10 virtual-link 1.1.1.1 authentication message-digest
area 10 virtual-link 1.1.1.1 message-digest-key 1 md5 cisco123
default-information originate always metric 150
!
ip route 0.0.0.0 0.0.0.0 FastEthernet 0/1
!
router ospf 10
network 10.10.0.0 0.0.255.255 area 0
network 10.20.0.0 0.0.255.255 area 0
network 10.30.0.0 0.0.255.255 area 0
network 10.40.0.0 0.0.255.255 area 0
network 10.50.0.0 0.0.255.255 area 0
network 172.16.3.0 0.0.0.3 area 0
!
router ospf 10
network 10.10.0.0 0.0.255.255 area 0
network 10.20.0.0 0.0.255.255 area 0
network 10.30.0.0 0.0.255.255 area 0
network 10.40.0.0 0.0.255.255 area 0
network 10.50.0.0 0.0.255.255 area 0
network 172.16.4.0 0.0.0.3 area 0
!
PPP 需求使用的是 CHAP 认证,CHAP 分单向人证和双向认证,需求中明确指定了主验方和被验方,即为单向验证,之后在 ISP 两边分别配置 PPP 握手协议即可。
username ISP password netlab
!
interface Serial 2/0
encapsulation PPP
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 cisco123
ip address 200.2.0.1 255.255.255.0
!
username RHQ password netlab
username RBR password netlab
!
interface Serial 2/0
encapsulation PPP
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 cisco123
ip address 200.1.0.2 255.255.255.0
!
interface Serial 3/0
encapsulation PPP
ppp authentication chap
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 cisco123
ip address 200.2.0.2 255.255.255.0
clock rate 64000
!
username ISP password netlab
!
interface Serial 3/0
encapsulation PPP
ppp authentication chap
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 cisco123
ip address 200.1.0.1 255.255.255.0
clock rate 64000
!
这一部分采坑比较多,思科模拟器上配置是好的,到了锐捷设备上是各种炸,最后尝试拨号时段时序,左后把协议从 l2tp 改成 any 之后稍稳定下来了。
配置其实就是四步走:
vpdn enable
!
vpdn-group L2TP
accept-dialin
protocol any
virtual-template 1
!
username vpn password cisco123
!
interface Loopback 99
ip address 10.99.0.254 255.255.0.0
!
interface Virtual-Template 1
ppp authentication chap
ip nat inside
ip unnumbered Loopback 99
peer default ip address pool VPN_POOL
!
ip local pool VPN_POOL 10.99.0.200 10.99.0.240
!
总公司和分公司都需要出公网,需要在 RHQ 和 RAR 上分别配置 NAT,可以通过端口复用的方法或者静态绑定的方法完成配置。
IPSEC VPN 配置需要对 NAT 的流量进行一次排流,并重新匹配,这两个过程一般都是先配置好 NAT 测试成功后继而在配置 IPSEC,为了方便,我讲最后的 NAT 和 IPSEC 的配置放在一起。
time-range WORK_TIME
periodic Daily 9:00 to 18:00
!
username ISP password netlab
!
ip access-list extended 100
10 deny ip 10.70.0.0 0.0.255.255 10.10.0.0 0.0.255.255
20 deny ip 10.70.0.0 0.0.255.255 10.20.0.0 0.0.255.255
30 deny ip 10.70.0.0 0.0.255.255 10.30.0.0 0.0.255.255
40 deny ip 10.70.0.0 0.0.255.255 10.40.0.0 0.0.255.255
50 deny ip 10.70.0.0 0.0.255.255 10.50.0.0 0.0.255.255
60 permit ip 10.70.0.0 0.0.255.255 any time-range WORK_TIME
!
ip access-list extended 120
10 permit ip 10.70.0.0 0.0.255.255 10.10.0.0 0.0.255.255
20 permit ip 10.70.0.0 0.0.255.255 10.20.0.0 0.0.255.255
30 permit ip 10.70.0.0 0.0.255.255 10.30.0.0 0.0.255.255
40 permit ip 10.70.0.0 0.0.255.255 10.40.0.0 0.0.255.255
50 permit ip 10.70.0.0 0.0.255.255 10.50.0.0 0.0.255.255
!
crypto isakmp policy 1
authentication pre-share
hash md5
!
crypto isakmp key 7 02404a241b096f517c address 61.160.5.6
crypto ipsec transform-set TRAN esp-3des esp-md5-hmac
crypto map VPN_MAP 1 ipsec-isakmp
set peer 61.160.5.6
set transform-set TRAN
match address 120
!
ip nat pool NAT_POOL 61.160.5.10 61.160.5.13 netmask 255.255.255.248
ip nat inside source list 100 pool NAT_POOL
!
interface FastEthernet 0/0
ip nat inside
ip address 10.70.0.254 255.255.0.0
!
interface FastEthernet 0/1
ip nat outside
ip address 61.160.5.14 255.255.255.248
crypto map VPN_MAP
!
ip access-list standard 1
10 permit 10.50.0.0 0.0.255.255
!
ip access-list extended 100
10 permit ip host 10.50.0.1 any
20 permit ip host 10.50.0.2 any
!
ip access-list extended 110
10 deny ip 10.10.0.0 0.0.255.255 10.70.0.0 0.0.255.255
20 deny ip 10.20.0.0 0.0.255.255 10.70.0.0 0.0.255.255
30 deny ip 10.30.0.0 0.0.255.255 10.70.0.0 0.0.255.255
40 deny ip 10.40.0.0 0.0.255.255 10.70.0.0 0.0.255.255
50 deny ip 10.50.0.0 0.0.255.255 10.70.0.0 0.0.255.255
60 permit ip 10.50.0.0 0.0.255.255 any
70 permit ip 10.40.0.0 0.0.255.255 any
80 permit ip 10.30.0.0 0.0.255.255 any
90 permit ip 10.20.0.0 0.0.255.255 any
100 permit ip 10.10.0.0 0.0.255.255 any
!
ip access-list extended 120
10 permit ip 10.10.0.0 0.0.255.255 10.70.0.0 0.0.255.255
20 permit ip 10.20.0.0 0.0.255.255 10.70.0.0 0.0.255.255
30 permit ip 10.30.0.0 0.0.255.255 10.70.0.0 0.0.255.255
40 permit ip 10.40.0.0 0.0.255.255 10.70.0.0 0.0.255.255
50 permit ip 10.50.0.0 0.0.255.255 10.70.0.0 0.0.255.255
!
crypto isakmp policy 1
authentication pre-share
hash md5
!
crypto isakmp key 7 03403e0b0531527d46 address 61.160.5.14
crypto ipsec transform-set TRAN esp-3des esp-md5-hmac
crypto map VPN_MAP 1 ipsec-isakmp
set peer 61.160.5.14
set transform-set TRAN
match address 120
!
interface Serial 2/0
ip nat outside
ip address 61.160.5.6 255.255.255.248
crypto map VPN_MAP
!
interface Serial 3/0
encapsulation PPP
ppp authentication chap
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 cisco123
ip address 200.1.0.1 255.255.255.0
clock rate 64000
!
interface FastEthernet 0/0
ip nat inside
ip address 172.16.3.2 255.255.255.252
!
interface FastEthernet 0/1
ip nat inside
ip address 172.16.4.2 255.255.255.252
!
ip nat pool NAT_POOL 61.160.5.3 61.160.5.5 netmask 255.255.255.248
ip nat inside source static tcp 10.50.0.1 80 61.160.5.6 80
ip nat inside source static tcp 10.50.0.2 20 61.160.5.6 20
ip nat inside source static tcp 10.50.0.2 21 61.160.5.6 21
ip nat inside source list 100 interface Serial 2/0 overload
ip nat inside source list 110 pool NAT_POOL
!
至此所有的配置都已经完成,总结一下有助于以后查阅。